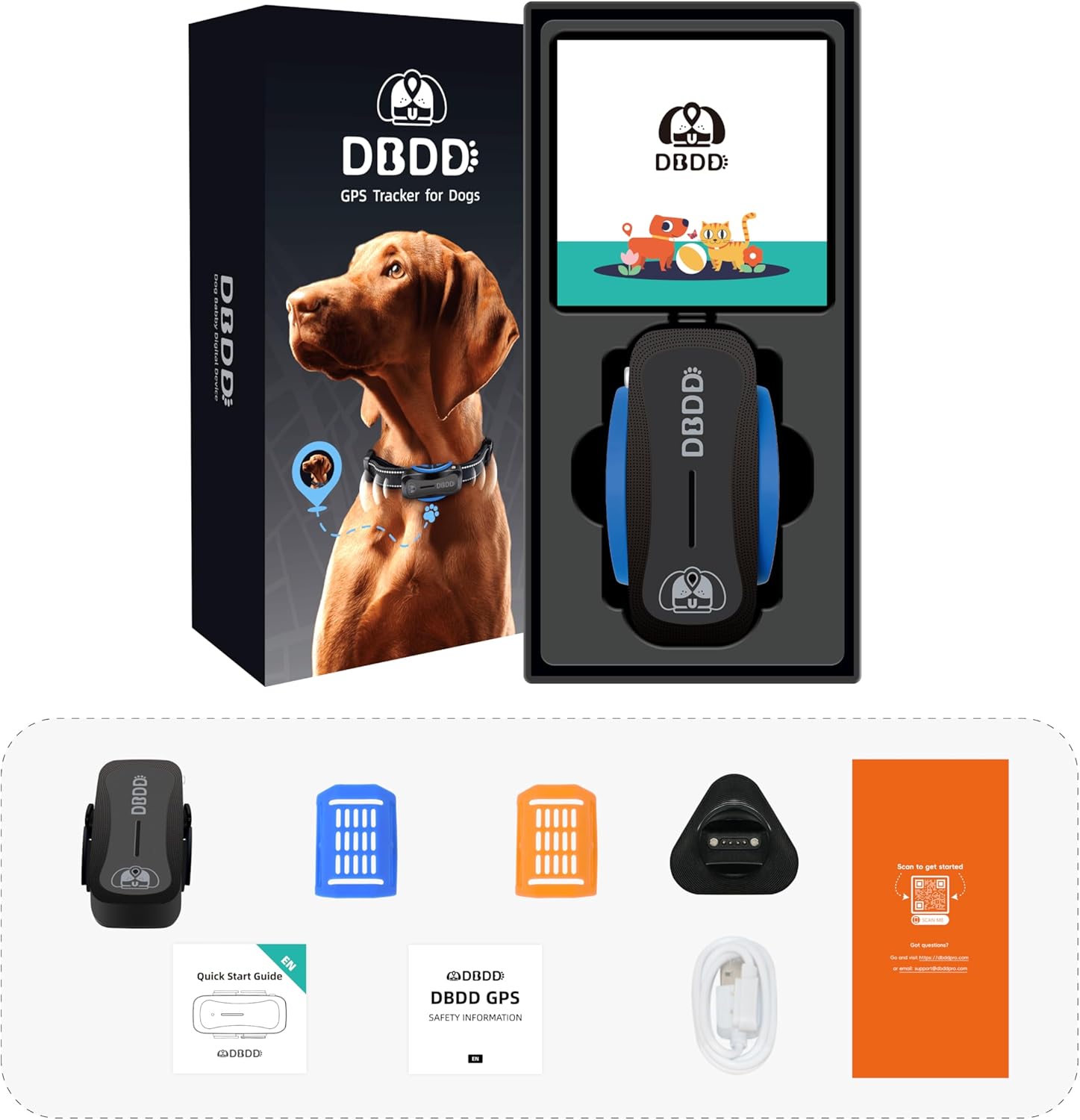
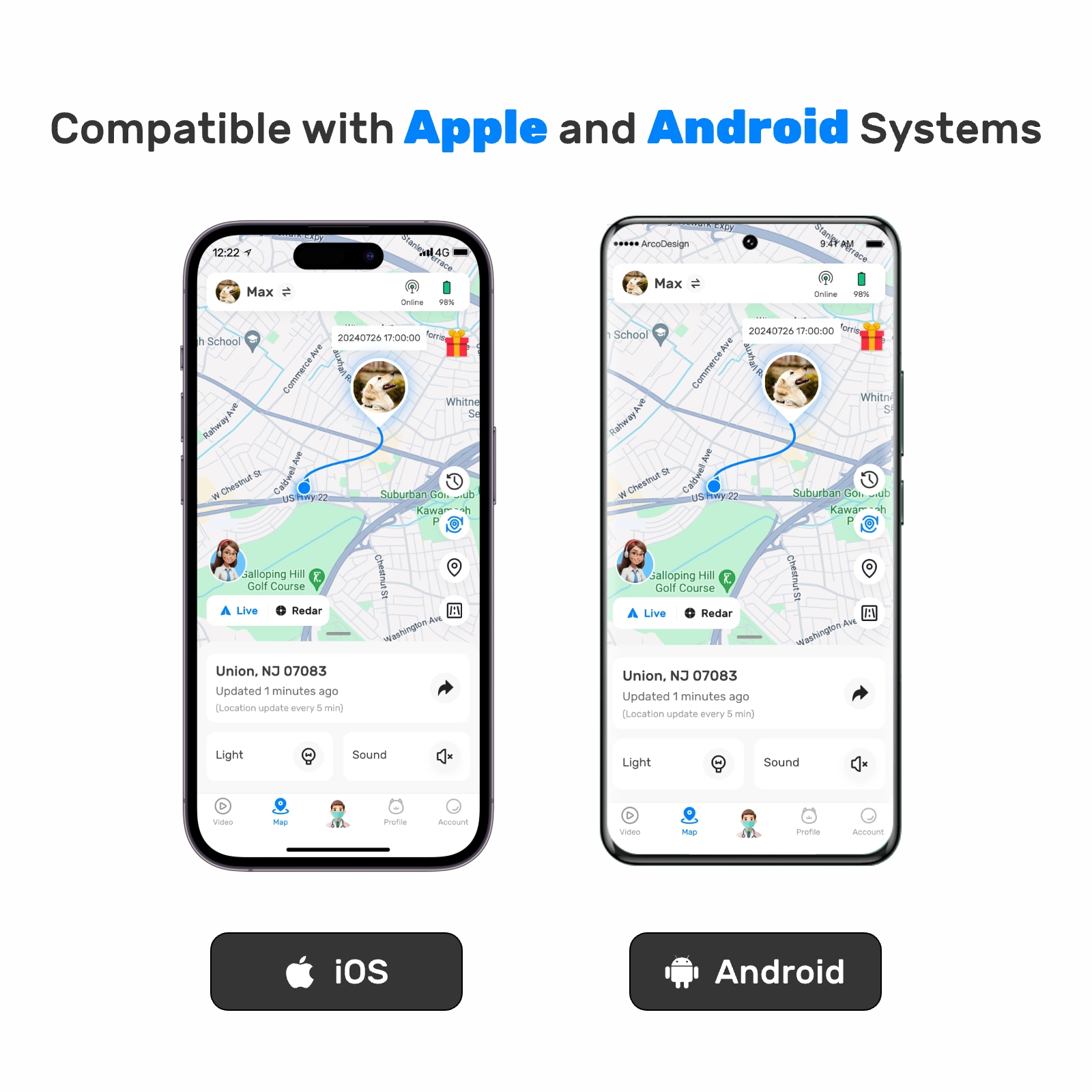
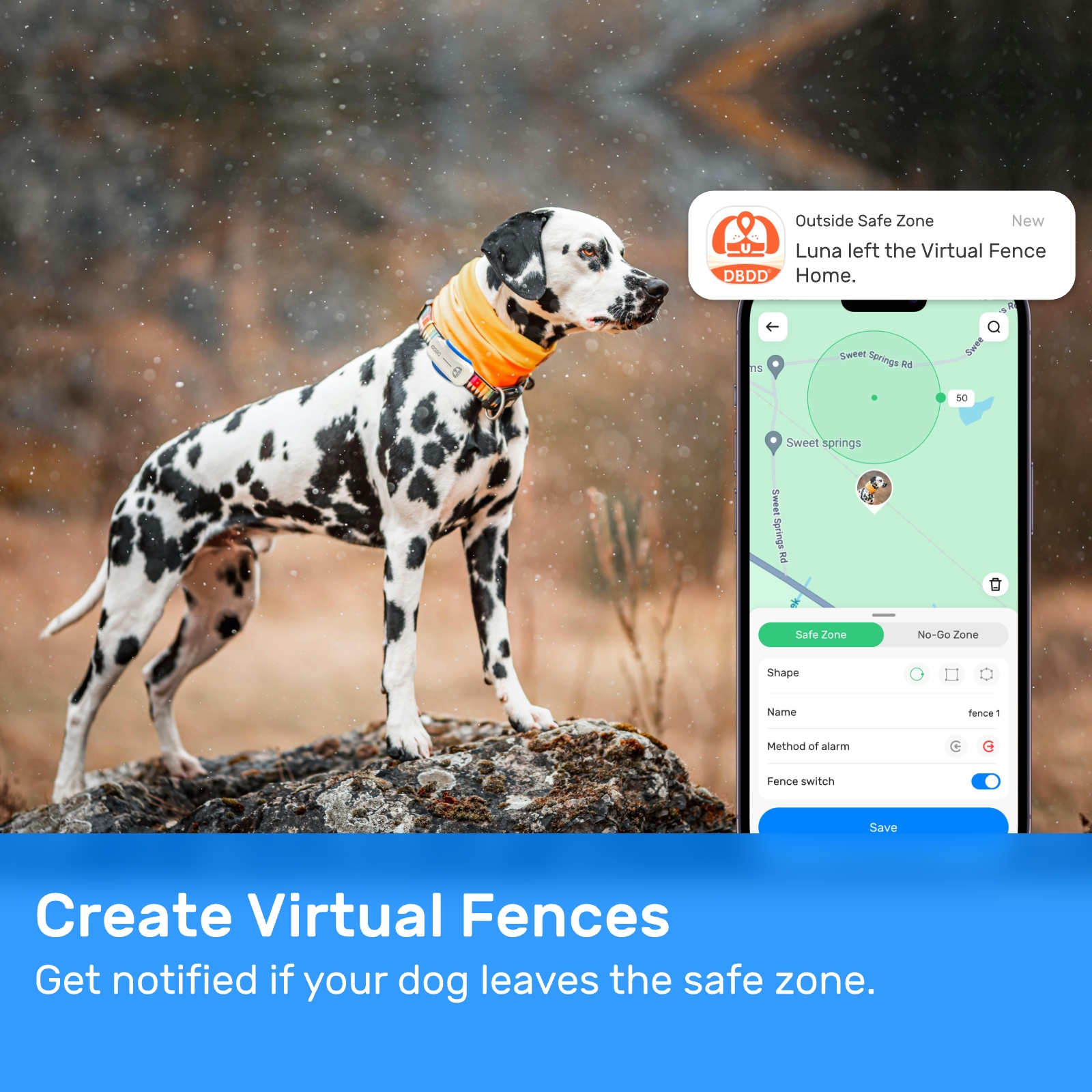
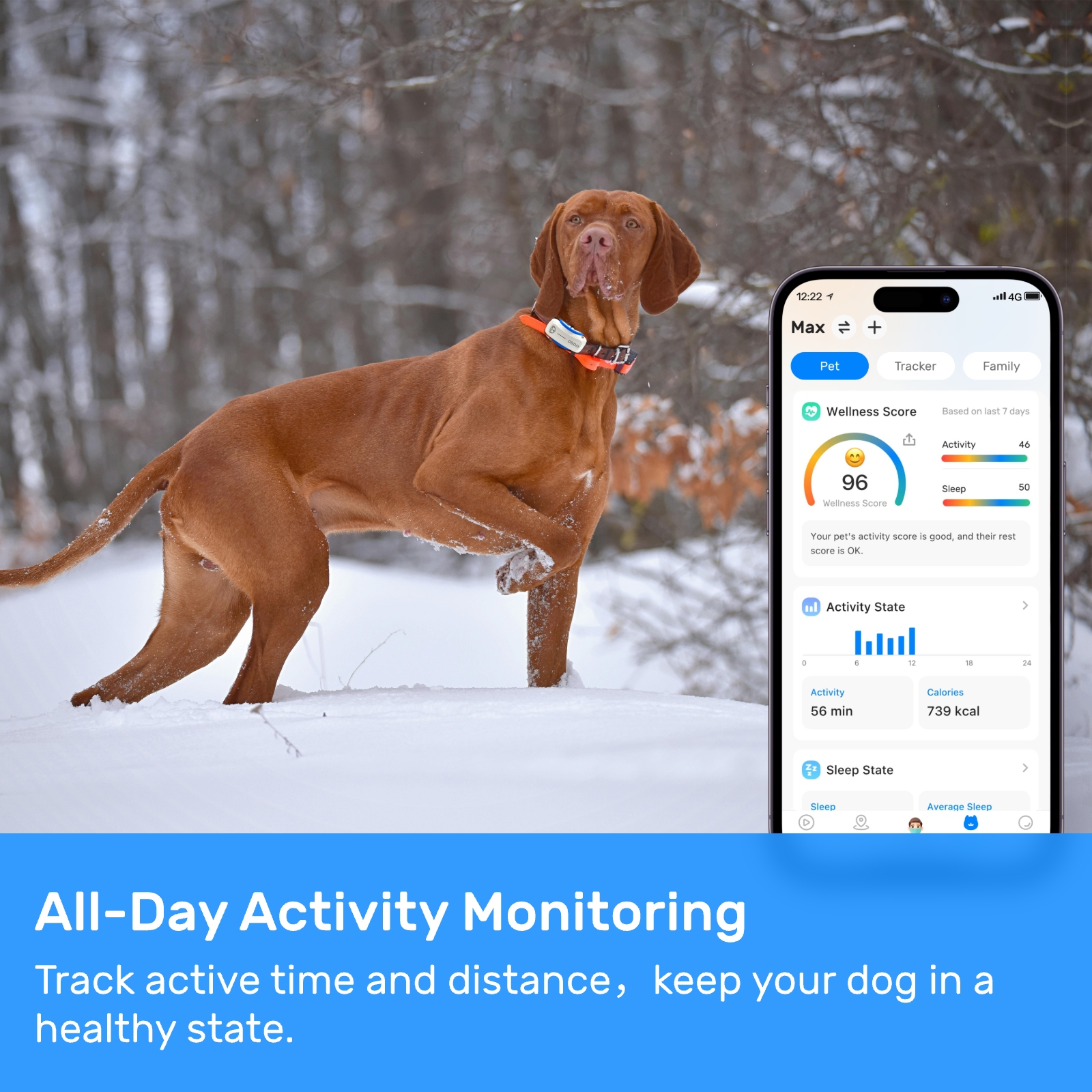
New ArrivalsBack in stock
elon musk doge treasury ban cybersecurity
 Limited Time Sale
Limited Time Sale
Until the end
00
00
00
Free shipping on orders over 999 ※)
If you buy it for 999 or more, you can buy it on behalf of the customer. There is no material for the number of hands.
If you buy it for 999 or more, you can buy it on behalf of the customer. There is no material for the number of hands.
There is stock in your local store.
Please note that the sales price and tax displayed may differ between online and in-store. Also, the product may be out of stock in-store.
Coupon giveaway!
| Control number |
New :D639370864 second hand :D639370864 |
Manufacturer | elon musk | release date | 2025-05-15 | List price | $36 | ||
|---|---|---|---|---|---|---|---|---|---|
| prototype | musk doge | ||||||||
| category | |||||||||
Pet Consumer Electronics#GPS Gadgets
In today's rapidly evolving technological landscape, the integration of GPS trackers with cellular coverage has become a cornerstone for various industries. From logistics to personal safety, these devices provide real-time location data that is essential for efficiency and security. However, as with any technology, the deployment of GPS trackers brings along its own set of challenges, particularly in the realm of cybersecurity. This article delves into the intricacies of mapping cellular coverage for GPS trackers, while also addressing the recent developments surrounding Elon Musk, the Doge Treasury ban, and their implications on cybersecurity.
The primary function of GPS trackers is to provide accurate location data by leveraging satellite signals. These trackers are then connected to cellular networks to transmit this information to a central server or user interface. The effectiveness of GPS trackers largely depends on the quality and extent of cellular coverage available. In areas with robust cellular infrastructure, GPS trackers can operate seamlessly, providing continuous updates on the location of assets or individuals. Conversely, in regions with limited or no cellular coverage, the functionality of these devices is severely hampered.
Mapping cellular coverage for GPS trackers involves several key considerations. First, it is crucial to understand the geographical distribution of cellular towers and their respective signal strengths. This information can be obtained through network surveys conducted by cellular service providers. By analyzing these surveys, one can identify potential gaps in coverage and devise strategies to mitigate them. For instance, deploying additional cellular towers or utilizing satellite communication as a backup can enhance the reliability of GPS trackers in remote areas.
Moreover, the choice of cellular network technology plays a significant role in determining the performance of GPS trackers. With the advent of 5G networks, there is an opportunity to significantly improve the speed and latency of data transmission. This advancement not only enhances the real-time capabilities of GPS trackers but also opens up new possibilities for integrating advanced features such as artificial intelligence and machine learning. However, the transition to 5G also poses challenges, as it requires substantial investment in infrastructure and may lead to temporary disruptions in service.
While the focus on improving cellular coverage for GPS trackers is paramount, it is equally important to address the cybersecurity concerns associated with these devices. GPS trackers often handle sensitive data, including the locations of high-value assets and personal information. As such, they become attractive targets for cybercriminals seeking to exploit vulnerabilities in the system. Recent incidents have highlighted the need for robust cybersecurity measures to protect against unauthorized access and data breaches.
In this context, the involvement of prominent figures like Elon Musk adds another layer of complexity to the discussion. Known for his innovative approach to technology and business, Musk has been at the forefront of several groundbreaking initiatives. One such initiative is the creation of a digital currency known as Dogecoin, which gained significant attention due to its humorous origins and unexpected rise in value. However, the association between Musk and Dogecoin has also sparked debates regarding the regulation and security of cryptocurrencies.

Recently, there have been calls for a ban on the Doge Treasury, a fund established to support the development and promotion of Dogecoin. Proponents of the ban argue that the treasury lacks transparency and could potentially be used for malicious purposes, including funding cyberattacks. Critics, on the other hand, contend that such a ban would stifle innovation and hinder the growth of decentralized finance. The debate surrounding the Doge Treasury ban underscores the broader challenges faced by the cryptocurrency industry in balancing freedom with accountability.

Elon Musk's influence extends beyond cryptocurrencies and into the realm of cybersecurity. As the CEO of Tesla and SpaceX, Musk has consistently emphasized the importance of securing critical infrastructure against cyber threats. His companies have implemented cutting-edge technologies to safeguard their operations, setting a benchmark for others in the industry. Furthermore, Musk has been vocal about the potential risks posed by artificial intelligence, advocating for responsible development and regulation to prevent misuse.
The intersection of GPS tracker technology, cellular coverage, and cybersecurity becomes even more relevant when considering the impact of global events such as the Doge Treasury ban. As governments and regulatory bodies grapple with the complexities of digital currencies, there is a growing recognition of the need for collaboration between stakeholders. This includes technology providers, financial institutions, and cybersecurity experts working together to establish frameworks that ensure the safe and ethical use of emerging technologies.
To effectively map cellular coverage for GPS trackers while addressing cybersecurity concerns, a multi-faceted approach is necessary. Firstly, there should be a concerted effort to enhance the resilience of cellular networks against cyber threats. This can be achieved through the implementation of advanced encryption protocols, regular security audits, and the adoption of zero-trust architectures. Additionally, fostering a culture of cybersecurity awareness among users of GPS trackers is crucial. Training programs and educational resources can empower individuals and organizations to recognize and respond to potential threats.
Another important aspect is the standardization of practices across the industry. By establishing common guidelines and best practices for the deployment of GPS trackers, manufacturers and service providers can ensure consistency in quality and security. Furthermore, collaboration with government agencies and international bodies can facilitate the sharing of intelligence and resources to combat cybercrime more effectively.
The role of artificial intelligence in enhancing both cellular coverage and cybersecurity cannot be overlooked. AI-driven algorithms can analyze vast amounts of data to predict coverage gaps and optimize network performance. Similarly, machine learning models can detect anomalies in network traffic, identifying potential cyberattacks before they cause significant damage. As these technologies continue to evolve, their integration into GPS tracker systems will become increasingly vital.
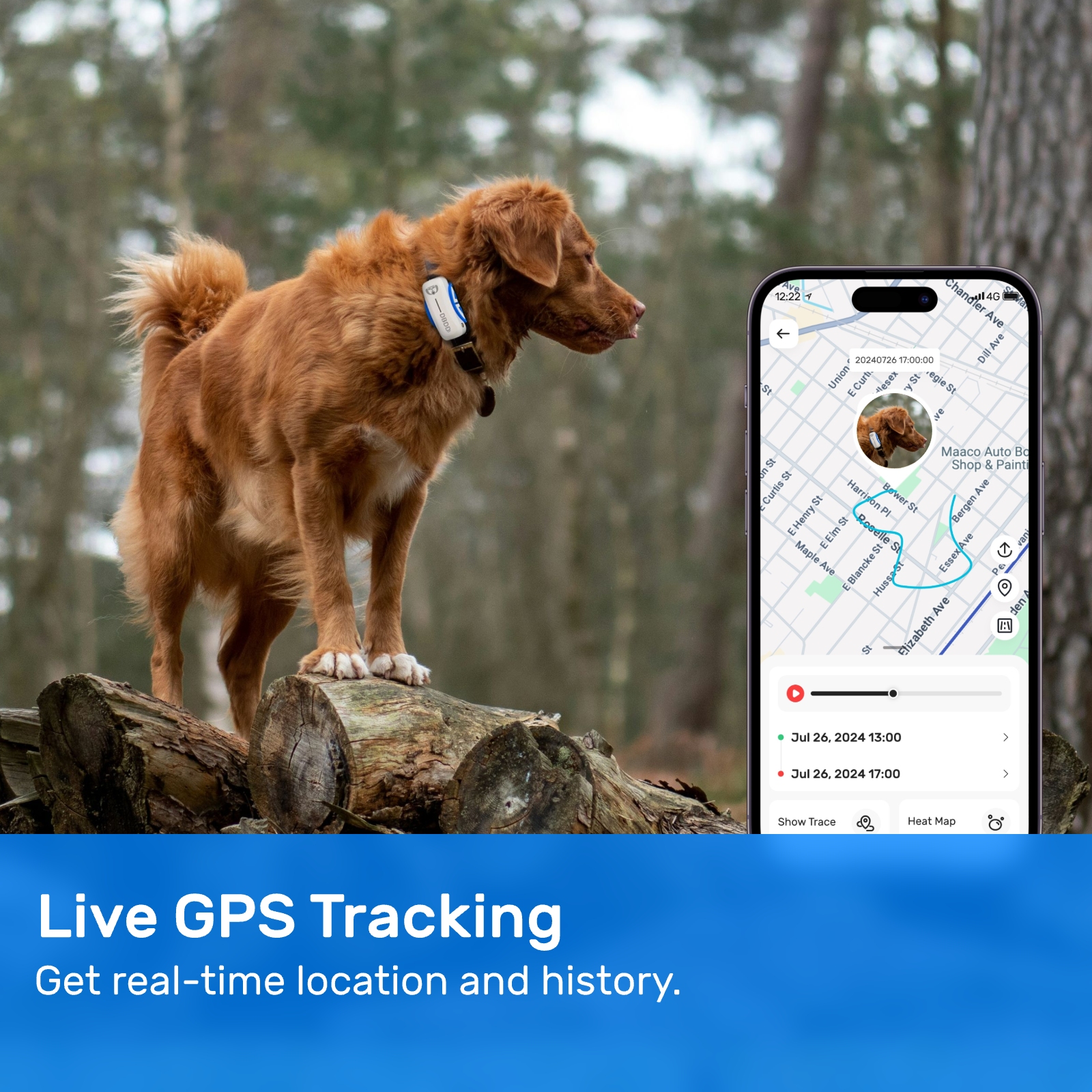
In conclusion, the mapping of cellular coverage for GPS trackers represents a complex yet rewarding endeavor. By addressing the challenges posed by limited coverage and cybersecurity threats, we can unlock the full potential of these devices. The discussions surrounding Elon Musk, the Doge Treasury ban, and cybersecurity serve as a reminder of the interconnected nature of modern technology. As we navigate this landscape, it is imperative to adopt a holistic approach that balances innovation with security, ensuring a safer and more connected future for all.

Update Time:2025-05-15 03:06:52
The primary function of GPS trackers is to provide accurate location data by leveraging satellite signals. These trackers are then connected to cellular networks to transmit this information to a central server or user interface. The effectiveness of GPS trackers largely depends on the quality and extent of cellular coverage available. In areas with robust cellular infrastructure, GPS trackers can operate seamlessly, providing continuous updates on the location of assets or individuals. Conversely, in regions with limited or no cellular coverage, the functionality of these devices is severely hampered.
Mapping cellular coverage for GPS trackers involves several key considerations. First, it is crucial to understand the geographical distribution of cellular towers and their respective signal strengths. This information can be obtained through network surveys conducted by cellular service providers. By analyzing these surveys, one can identify potential gaps in coverage and devise strategies to mitigate them. For instance, deploying additional cellular towers or utilizing satellite communication as a backup can enhance the reliability of GPS trackers in remote areas.
Moreover, the choice of cellular network technology plays a significant role in determining the performance of GPS trackers. With the advent of 5G networks, there is an opportunity to significantly improve the speed and latency of data transmission. This advancement not only enhances the real-time capabilities of GPS trackers but also opens up new possibilities for integrating advanced features such as artificial intelligence and machine learning. However, the transition to 5G also poses challenges, as it requires substantial investment in infrastructure and may lead to temporary disruptions in service.
While the focus on improving cellular coverage for GPS trackers is paramount, it is equally important to address the cybersecurity concerns associated with these devices. GPS trackers often handle sensitive data, including the locations of high-value assets and personal information. As such, they become attractive targets for cybercriminals seeking to exploit vulnerabilities in the system. Recent incidents have highlighted the need for robust cybersecurity measures to protect against unauthorized access and data breaches.
In this context, the involvement of prominent figures like Elon Musk adds another layer of complexity to the discussion. Known for his innovative approach to technology and business, Musk has been at the forefront of several groundbreaking initiatives. One such initiative is the creation of a digital currency known as Dogecoin, which gained significant attention due to its humorous origins and unexpected rise in value. However, the association between Musk and Dogecoin has also sparked debates regarding the regulation and security of cryptocurrencies.

Recently, there have been calls for a ban on the Doge Treasury, a fund established to support the development and promotion of Dogecoin. Proponents of the ban argue that the treasury lacks transparency and could potentially be used for malicious purposes, including funding cyberattacks. Critics, on the other hand, contend that such a ban would stifle innovation and hinder the growth of decentralized finance. The debate surrounding the Doge Treasury ban underscores the broader challenges faced by the cryptocurrency industry in balancing freedom with accountability.

Elon Musk's influence extends beyond cryptocurrencies and into the realm of cybersecurity. As the CEO of Tesla and SpaceX, Musk has consistently emphasized the importance of securing critical infrastructure against cyber threats. His companies have implemented cutting-edge technologies to safeguard their operations, setting a benchmark for others in the industry. Furthermore, Musk has been vocal about the potential risks posed by artificial intelligence, advocating for responsible development and regulation to prevent misuse.
The intersection of GPS tracker technology, cellular coverage, and cybersecurity becomes even more relevant when considering the impact of global events such as the Doge Treasury ban. As governments and regulatory bodies grapple with the complexities of digital currencies, there is a growing recognition of the need for collaboration between stakeholders. This includes technology providers, financial institutions, and cybersecurity experts working together to establish frameworks that ensure the safe and ethical use of emerging technologies.
To effectively map cellular coverage for GPS trackers while addressing cybersecurity concerns, a multi-faceted approach is necessary. Firstly, there should be a concerted effort to enhance the resilience of cellular networks against cyber threats. This can be achieved through the implementation of advanced encryption protocols, regular security audits, and the adoption of zero-trust architectures. Additionally, fostering a culture of cybersecurity awareness among users of GPS trackers is crucial. Training programs and educational resources can empower individuals and organizations to recognize and respond to potential threats.
Another important aspect is the standardization of practices across the industry. By establishing common guidelines and best practices for the deployment of GPS trackers, manufacturers and service providers can ensure consistency in quality and security. Furthermore, collaboration with government agencies and international bodies can facilitate the sharing of intelligence and resources to combat cybercrime more effectively.
The role of artificial intelligence in enhancing both cellular coverage and cybersecurity cannot be overlooked. AI-driven algorithms can analyze vast amounts of data to predict coverage gaps and optimize network performance. Similarly, machine learning models can detect anomalies in network traffic, identifying potential cyberattacks before they cause significant damage. As these technologies continue to evolve, their integration into GPS tracker systems will become increasingly vital.

In conclusion, the mapping of cellular coverage for GPS trackers represents a complex yet rewarding endeavor. By addressing the challenges posed by limited coverage and cybersecurity threats, we can unlock the full potential of these devices. The discussions surrounding Elon Musk, the Doge Treasury ban, and cybersecurity serve as a reminder of the interconnected nature of modern technology. As we navigate this landscape, it is imperative to adopt a holistic approach that balances innovation with security, ensuring a safer and more connected future for all.

Update Time:2025-05-15 03:06:52
Correction of product information
If you notice any omissions or errors in the product information on this page, please use the correction request form below.
Correction Request Form