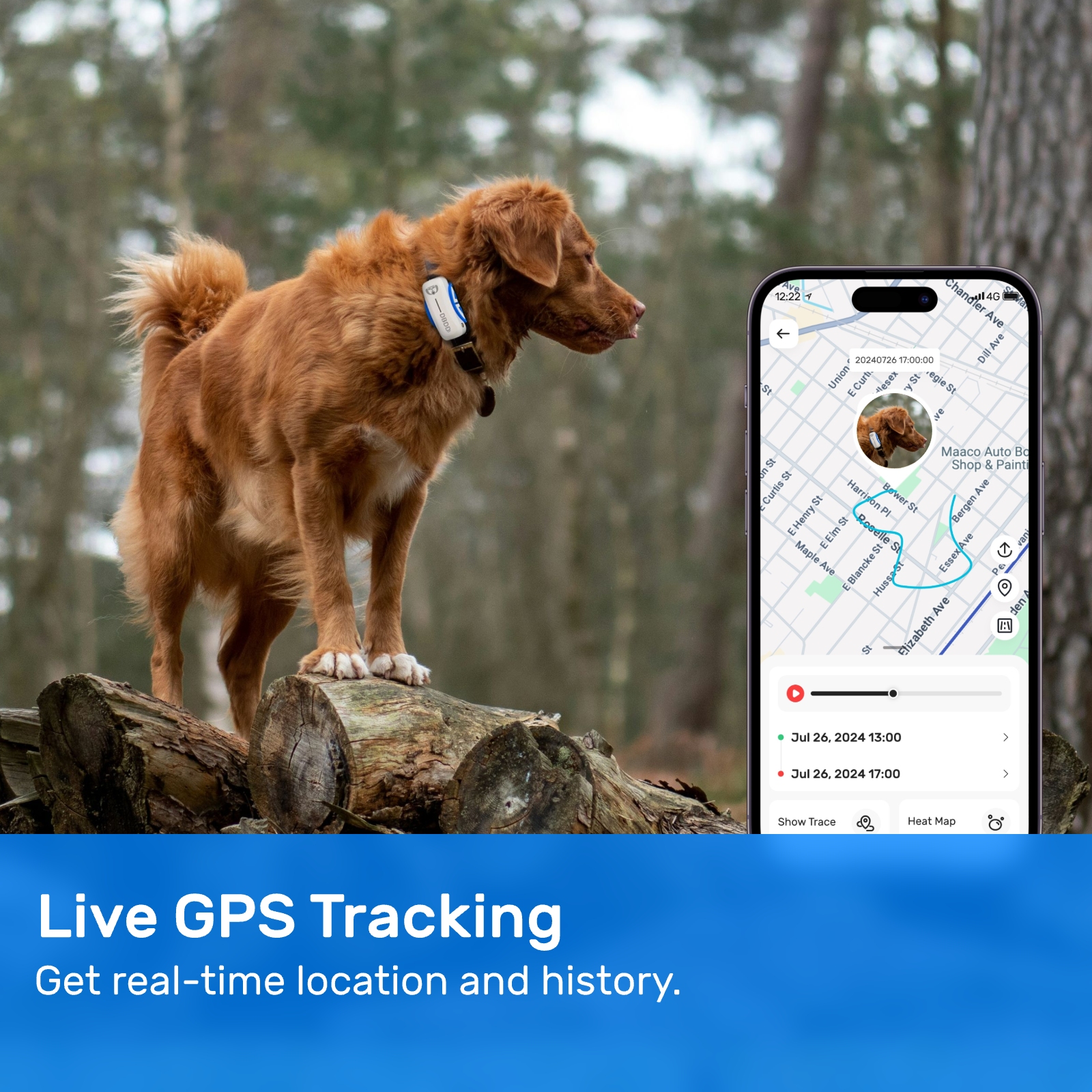
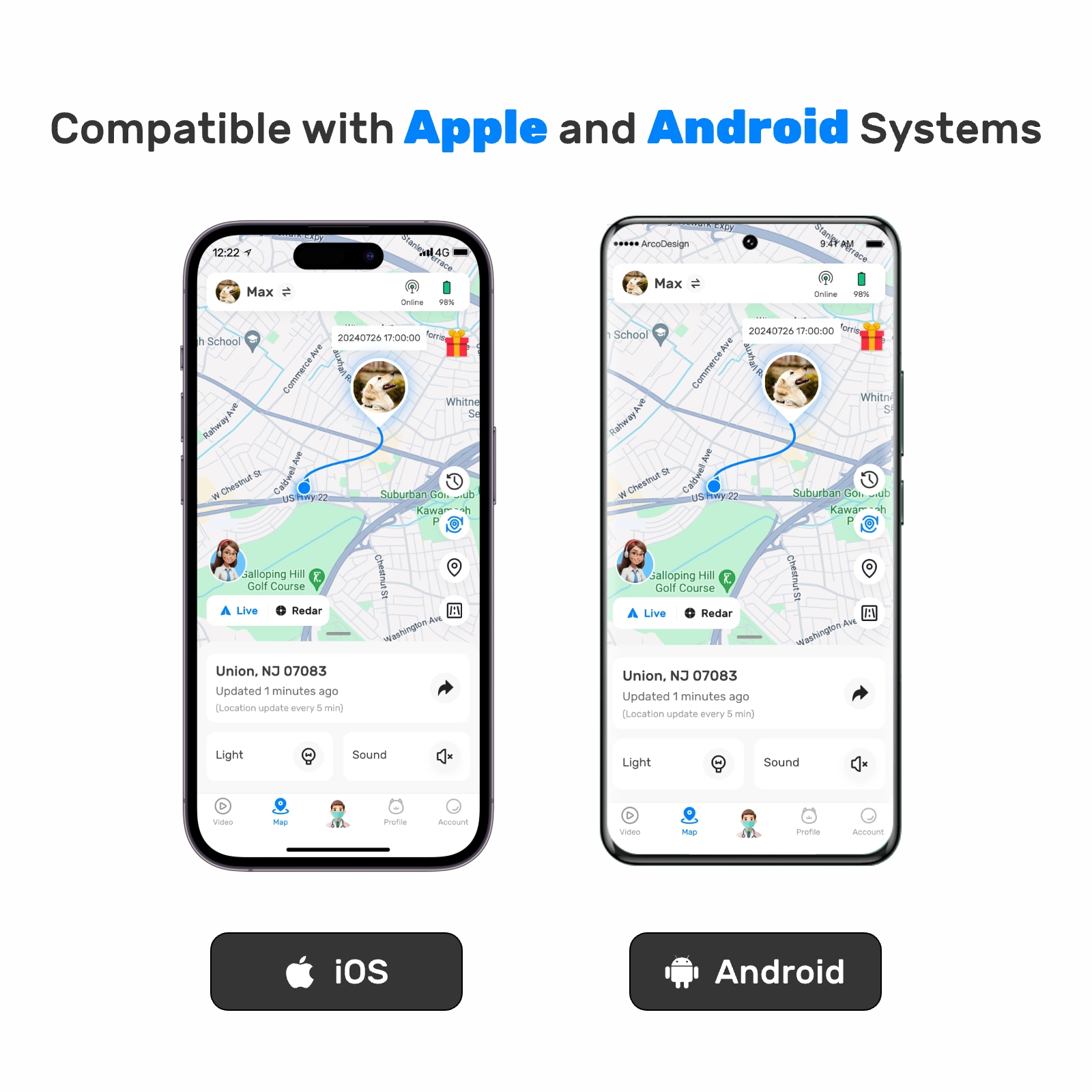
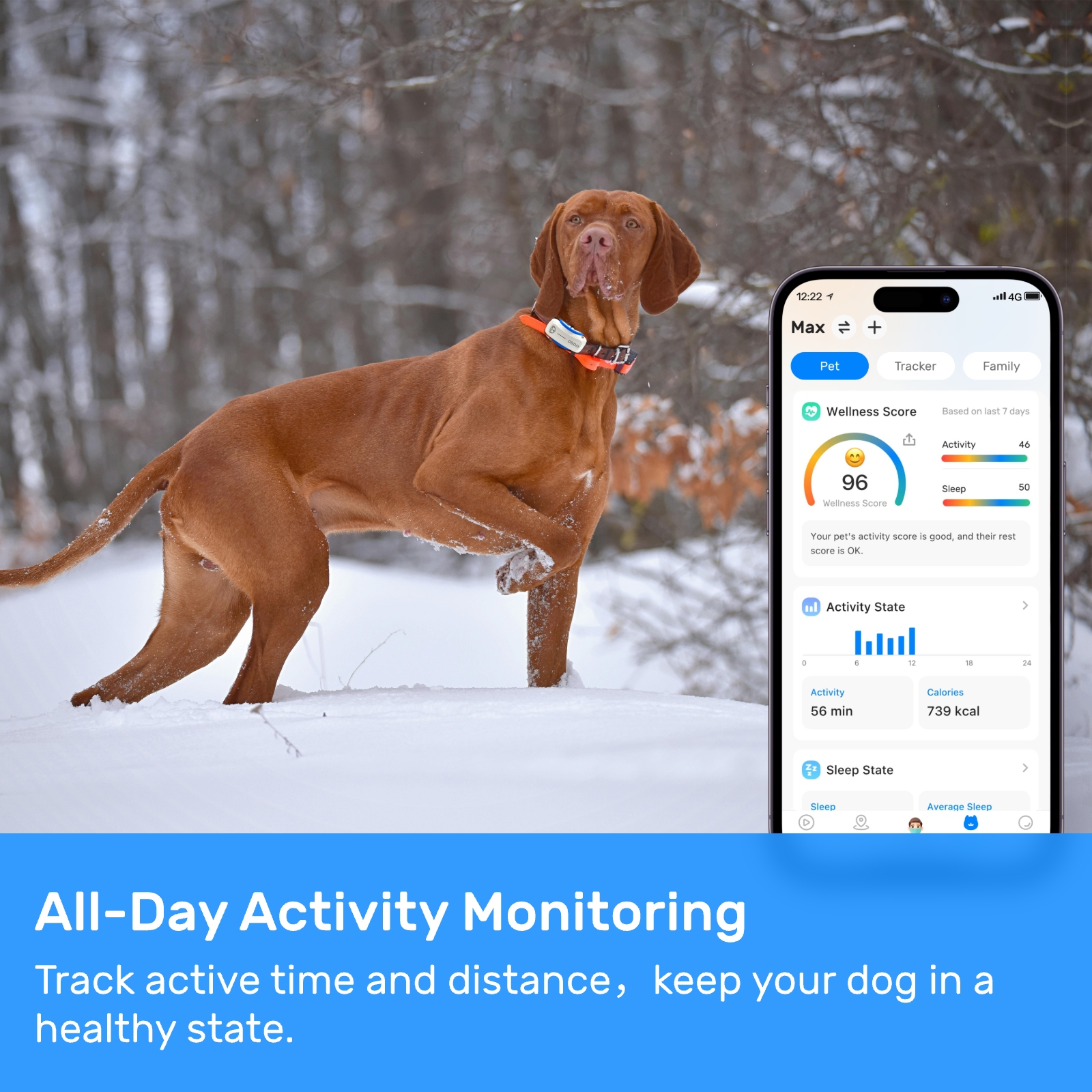
New ArrivalsBack in stock
doge website hacked
 Limited Time Sale
Limited Time Sale
Until the end
00
00
00
Free shipping on orders over 999 ※)
If you buy it for 999 or more, you can buy it on behalf of the customer. There is no material for the number of hands.
If you buy it for 999 or more, you can buy it on behalf of the customer. There is no material for the number of hands.
There is stock in your local store.
Please note that the sales price and tax displayed may differ between online and in-store. Also, the product may be out of stock in-store.
Coupon giveaway!
| Control number |
New :D756257646 second hand :D756257646 |
Manufacturer | doge website | release date | 2025-05-15 | List price | $34 | ||
|---|---|---|---|---|---|---|---|---|---|
| prototype | website hacked | ||||||||
| category | |||||||||
Senior Care#Elderly Pet Monitoring
In today's fast-paced digital world, the importance of GPS tracking and cellular coverage cannot be overstated. GPS trackers are essential for various applications, such as fleet management, asset tracking, and personal safety. These devices rely on cellular networks to communicate their location data to designated servers or applications. However, recent events, such as the hacking of a doge website, have raised concerns about the security and reliability of these systems. This article will explore the intricacies of cellular coverage for GPS trackers and the implications of cyber-attacks on their functionality.
Cellular Coverage for GPS Trackers

GPS trackers use cellular networks to transmit data, which means that their performance is heavily dependent on the quality and reach of these networks. Cellular coverage is determined by several factors, including the density of cell towers, the strength of signals, and the geographical location of the device.
1. Signal Strength: The signal strength of a cellular network is measured in decibels (dBm). A stronger signal results in faster data transmission and better overall performance. GPS trackers require a minimum signal strength to function effectively. In most cases, a signal strength of -90 dBm or higher is considered adequate for reliable GPS tracking.
2. Network Density: The density of cell towers in an area directly impacts the quality of cellular coverage. More cell towers mean more signal strength and better coverage. In urban areas, where cell towers are densely packed, GPS trackers can function optimally. However, in rural or remote areas, the lack of cell towers can lead to weak signals and poor GPS tracking performance.
3. Geographical Location: The geographical location of a GPS tracker plays a crucial role in determining its cellular coverage. Terrain, weather conditions, and the presence of obstructions like buildings or mountains can all affect signal strength. GPS trackers may experience weak signals or even complete signal loss in areas with poor cellular coverage.
Mapping Cellular Coverage for GPS Trackers
Mapping cellular coverage for GPS trackers involves collecting data on signal strength, network density, and geographical location. This information can be used to create a comprehensive map that highlights areas with strong and weak cellular coverage. Several tools and techniques can be employed to achieve this:
1. Drive Tests: Drive tests involve using a vehicle equipped with GPS trackers and signal strength measurement devices to collect data on cellular coverage. This method provides real-time information on signal strength and can be used to identify areas with weak coverage.
2. Network Simulation: Network simulation software can be used to model the behavior of cellular networks under various conditions. This method can help predict signal strength and coverage in different locations, allowing for the identification of areas with poor coverage.
3. Crowdsourcing: Crowdsourcing involves leveraging data from multiple GPS trackers to create a comprehensive map of cellular coverage. Users can share their signal strength data, which can then be aggregated and analyzed to identify patterns and trends in coverage.
Implications of the Doge Website Hacked on GPS Trackers
The recent hacking of a doge website has raised concerns about the security and reliability of GPS trackers. While the hack itself did not directly affect GPS trackers, it highlights the potential vulnerabilities of systems that rely on internet connectivity. GPS trackers, which use cellular networks to transmit data, are also susceptible to cyber-attacks.
1. Data Breaches: GPS trackers collect sensitive information, such as location data and user identification. Cybercriminals can exploit vulnerabilities in these systems to access and steal this data, leading to privacy breaches and potential misuse of information.
2. Service Disruption: Hacking attempts can lead to disruptions in the functioning of GPS trackers. For example, an attacker could flood a GPS tracking server with excessive traffic, causing it to crash and rendering the tracker inoperable.
3. Unauthorized Access: GPS trackers can be accessed remotely, which means that unauthorized individuals can potentially gain control over the device. This could lead to the tracking of unauthorized individuals or the manipulation of location data.
Mitigating the Risks of Cyber-Attacks on GPS Trackers
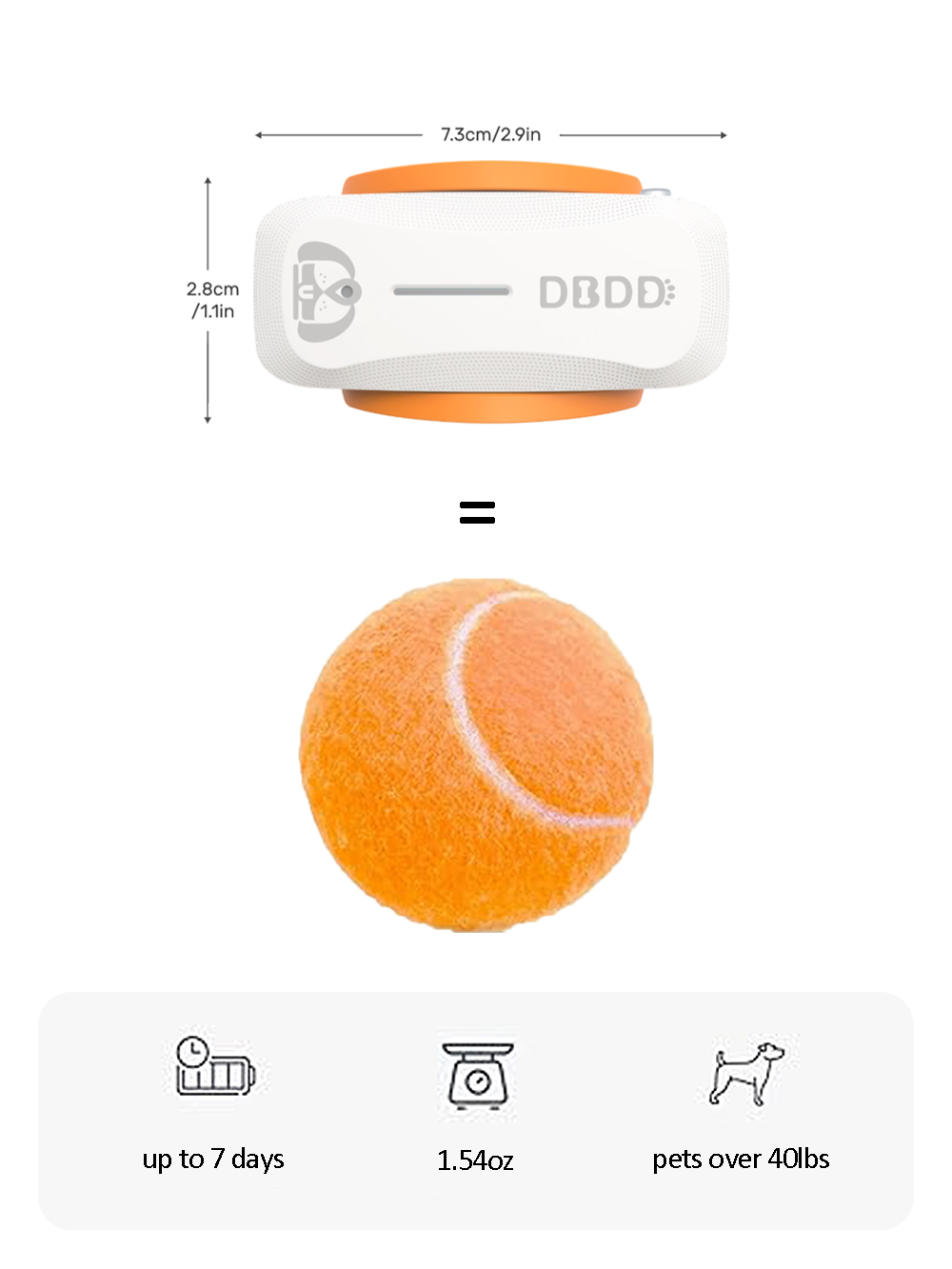
To ensure the security and reliability of GPS trackers, several measures can be taken to mitigate the risks associated with cyber-attacks:
1. Secure Communication: GPS trackers should use secure communication protocols, such as HTTPS, to encrypt data transmitted between the device and the server. This can help protect sensitive information from being intercepted by unauthorized parties.
2. Regular Updates: GPS trackers should receive regular software updates to patch any vulnerabilities and improve overall security. Manufacturers should prioritize the release of security updates and encourage users to install them promptly.
3. Strong Authentication: GPS trackers should implement strong authentication mechanisms, such as two-factor authentication, to prevent unauthorized access. This can help protect the device from being accessed by attackers even if they manage to bypass other security measures.

4. Network Monitoring: GPS tracking servers should be monitored regularly for any signs of unusual activity, such as excessive traffic or unauthorized access attempts. This can help detect and respond to potential cyber-attacks more quickly.
5. Education and Awareness: Users should be educated about the risks associated with GPS trackers and the importance of maintaining their security. This can include
Update Time:2025-05-15 07:38:26
Cellular Coverage for GPS Trackers

GPS trackers use cellular networks to transmit data, which means that their performance is heavily dependent on the quality and reach of these networks. Cellular coverage is determined by several factors, including the density of cell towers, the strength of signals, and the geographical location of the device.
1. Signal Strength: The signal strength of a cellular network is measured in decibels (dBm). A stronger signal results in faster data transmission and better overall performance. GPS trackers require a minimum signal strength to function effectively. In most cases, a signal strength of -90 dBm or higher is considered adequate for reliable GPS tracking.
2. Network Density: The density of cell towers in an area directly impacts the quality of cellular coverage. More cell towers mean more signal strength and better coverage. In urban areas, where cell towers are densely packed, GPS trackers can function optimally. However, in rural or remote areas, the lack of cell towers can lead to weak signals and poor GPS tracking performance.
3. Geographical Location: The geographical location of a GPS tracker plays a crucial role in determining its cellular coverage. Terrain, weather conditions, and the presence of obstructions like buildings or mountains can all affect signal strength. GPS trackers may experience weak signals or even complete signal loss in areas with poor cellular coverage.
Mapping Cellular Coverage for GPS Trackers
Mapping cellular coverage for GPS trackers involves collecting data on signal strength, network density, and geographical location. This information can be used to create a comprehensive map that highlights areas with strong and weak cellular coverage. Several tools and techniques can be employed to achieve this:
1. Drive Tests: Drive tests involve using a vehicle equipped with GPS trackers and signal strength measurement devices to collect data on cellular coverage. This method provides real-time information on signal strength and can be used to identify areas with weak coverage.
2. Network Simulation: Network simulation software can be used to model the behavior of cellular networks under various conditions. This method can help predict signal strength and coverage in different locations, allowing for the identification of areas with poor coverage.
3. Crowdsourcing: Crowdsourcing involves leveraging data from multiple GPS trackers to create a comprehensive map of cellular coverage. Users can share their signal strength data, which can then be aggregated and analyzed to identify patterns and trends in coverage.
Implications of the Doge Website Hacked on GPS Trackers
The recent hacking of a doge website has raised concerns about the security and reliability of GPS trackers. While the hack itself did not directly affect GPS trackers, it highlights the potential vulnerabilities of systems that rely on internet connectivity. GPS trackers, which use cellular networks to transmit data, are also susceptible to cyber-attacks.
1. Data Breaches: GPS trackers collect sensitive information, such as location data and user identification. Cybercriminals can exploit vulnerabilities in these systems to access and steal this data, leading to privacy breaches and potential misuse of information.
2. Service Disruption: Hacking attempts can lead to disruptions in the functioning of GPS trackers. For example, an attacker could flood a GPS tracking server with excessive traffic, causing it to crash and rendering the tracker inoperable.
3. Unauthorized Access: GPS trackers can be accessed remotely, which means that unauthorized individuals can potentially gain control over the device. This could lead to the tracking of unauthorized individuals or the manipulation of location data.
Mitigating the Risks of Cyber-Attacks on GPS Trackers

To ensure the security and reliability of GPS trackers, several measures can be taken to mitigate the risks associated with cyber-attacks:
1. Secure Communication: GPS trackers should use secure communication protocols, such as HTTPS, to encrypt data transmitted between the device and the server. This can help protect sensitive information from being intercepted by unauthorized parties.
2. Regular Updates: GPS trackers should receive regular software updates to patch any vulnerabilities and improve overall security. Manufacturers should prioritize the release of security updates and encourage users to install them promptly.
3. Strong Authentication: GPS trackers should implement strong authentication mechanisms, such as two-factor authentication, to prevent unauthorized access. This can help protect the device from being accessed by attackers even if they manage to bypass other security measures.

4. Network Monitoring: GPS tracking servers should be monitored regularly for any signs of unusual activity, such as excessive traffic or unauthorized access attempts. This can help detect and respond to potential cyber-attacks more quickly.
5. Education and Awareness: Users should be educated about the risks associated with GPS trackers and the importance of maintaining their security. This can include
Update Time:2025-05-15 07:38:26
Correction of product information
If you notice any omissions or errors in the product information on this page, please use the correction request form below.
Correction Request Form